Canal Mail Corp: Your Hub for Daily Insights
Explore the latest news, tips, and trends across various topics.
Bitcoin Transactions: Where Privacy Meets the Blockchain
Discover how Bitcoin transactions balance privacy and transparency on the blockchain. Uncover secrets that could change your crypto journey!
Understanding Bitcoin Privacy: How Transactions Work on the Blockchain
Understanding Bitcoin Privacy is crucial for navigating the world of cryptocurrency. Transactions on the blockchain are recorded on a public ledger, which means that although users' identities remain pseudonymous, transaction amounts and addresses are still visible to everyone. This transparency could lead to privacy concerns for those wishing to keep their financial activities discreet. To mitigate these risks, users often employ various strategies, such as using new addresses for each transaction or utilizing more advanced privacy-focused tools like Tor or mixers.
To comprehend how Bitcoin transactions work on the blockchain, it's essential to understand the process of transaction verification. When a transaction is initiated, it is broadcast to the network, where miners validate it through a consensus mechanism known as Proof of Work. Each confirmed transaction is then grouped into a block and added to the blockchain. This process not only guarantees the integrity of each transaction but also ensures that once they are recorded, they cannot be altered or deleted, further enhancing the concept of Bitcoin privacy by facilitating trust in decentralized financial transactions.
Counter-Strike is a popular tactical first-person shooter game that pits two teams against each other: terrorists and counter-terrorists. Players engage in various objective-based game modes, where teamwork and strategy are essential for success. For those looking to enhance their gaming experience, using a cloudbet promo code can provide valuable bonuses and perks.
Top Strategies for Enhancing Privacy in Bitcoin Transactions
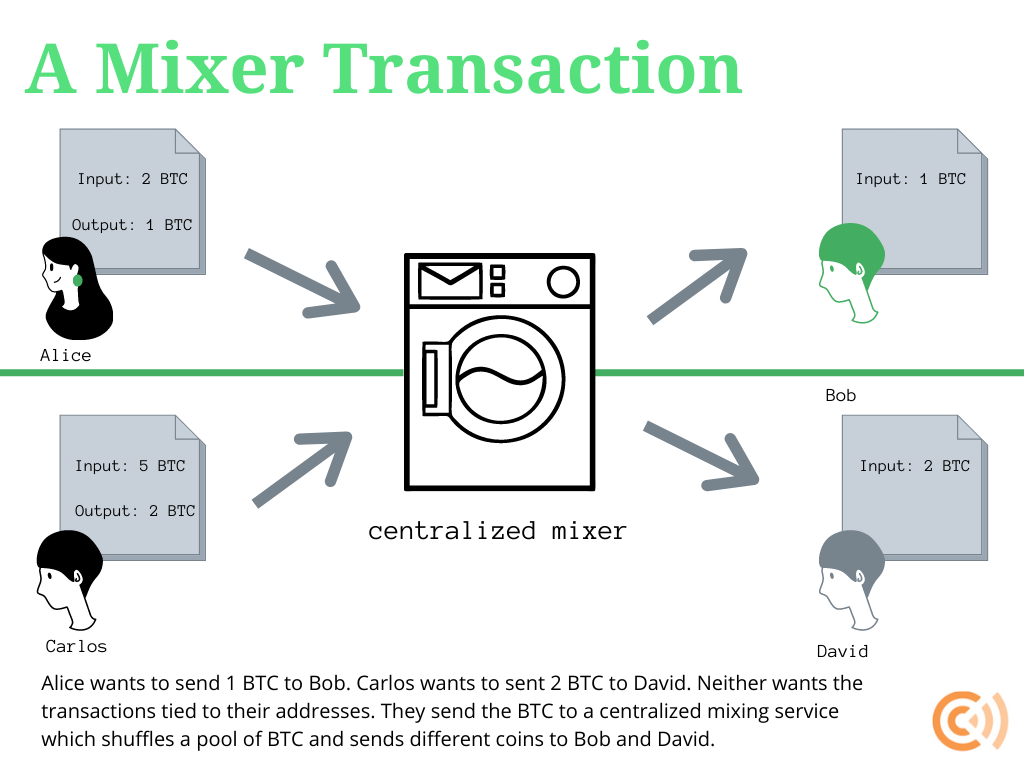
As Bitcoin gains popularity, ensuring privacy in transactions has become paramount for users concerned about their financial security. One effective strategy is to employ coin mixers or tumbler services, which obfuscate transaction trails by mixing coins from various users. This process makes it difficult for third parties to trace transaction origins, enhancing the privacy of individuals. Additionally, utilizing lightning network can significantly improve transaction confidentiality by establishing a second-layer payment protocol that allows for faster and more private transactions, effectively minimizing exposure on the Bitcoin blockchain.
Another critical strategy involves using privacy-focused wallets. These wallets are designed to enhance user anonymity and may incorporate features like address generation and transaction splitting. For those who want even more privacy, consider employing VPNs or Tor networks while making transactions, as they help conceal the user's IP address from prying eyes. Lastly, engaging in practices such as using segregated witness (SegWit) addresses and avoiding the reuse of addresses can bolster privacy in Bitcoin transactions, making them less susceptible to tracking.
Is Bitcoin Truly Anonymous? Debunking Myths and Misconceptions
The notion that Bitcoin is completely anonymous is a common misconception. In reality, Bitcoin transactions are recorded on a public ledger known as the blockchain, which means that every transaction is transparent and traceable. While user identities are not directly tied to wallet addresses, the data can be de-anonymized through various means, especially when users choose to exchange Bitcoin for fiat currency or link their wallet to personal information. This process has led to numerous cases where authorities were able to trace criminal activities back to individuals using advanced analysis techniques.
Furthermore, many users mistakenly believe that using Bitcoin mixing services can safeguard their anonymity completely. Although these services can obscure the origins of cryptocurrencies, they do not offer foolproof privacy and still carry inherent risks. Moreover, exchanges and platforms are increasingly adopting stringent Know Your Customer (KYC) policies, further diminishing the level of anonymity. Ultimately, while Bitcoin provides more privacy than traditional financial systems, understanding its limitations is crucial for users who wish to protect their identities.